
Enumeration
Nmap Scan
I started with a standard scan using Nmap:
| |
Rsync
I noticed that the machine exposes an rsync service. I enumerated available modules:
| |
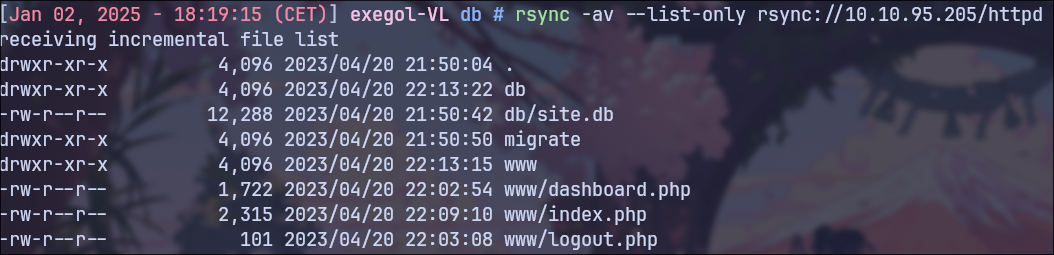
I found a module named httpd:
| |
The rsync service contains an application backup. I downloaded it with:
| |
Application Analysis
PHP
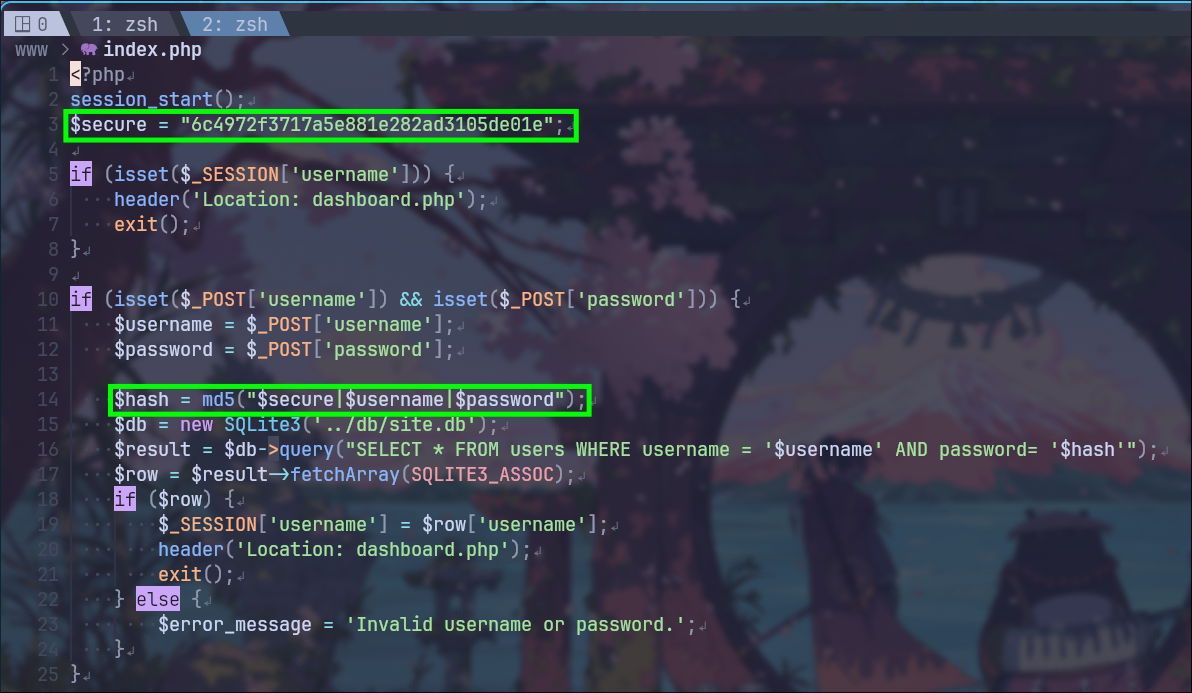
Reviewing the PHP code, I found a secret and the logic used to generate password hashes.
Database
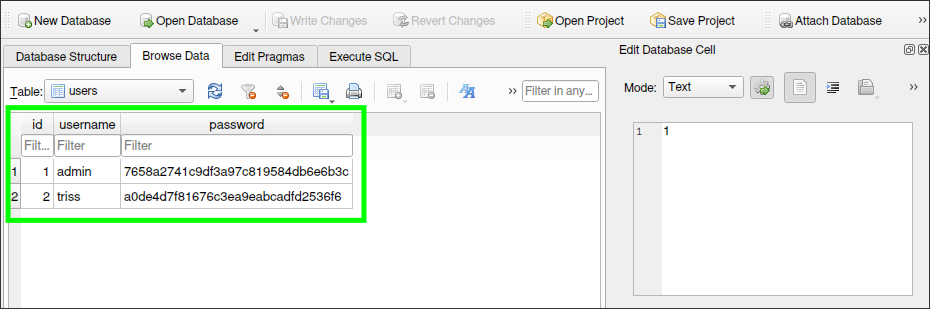
The database contains password hashes for two users.
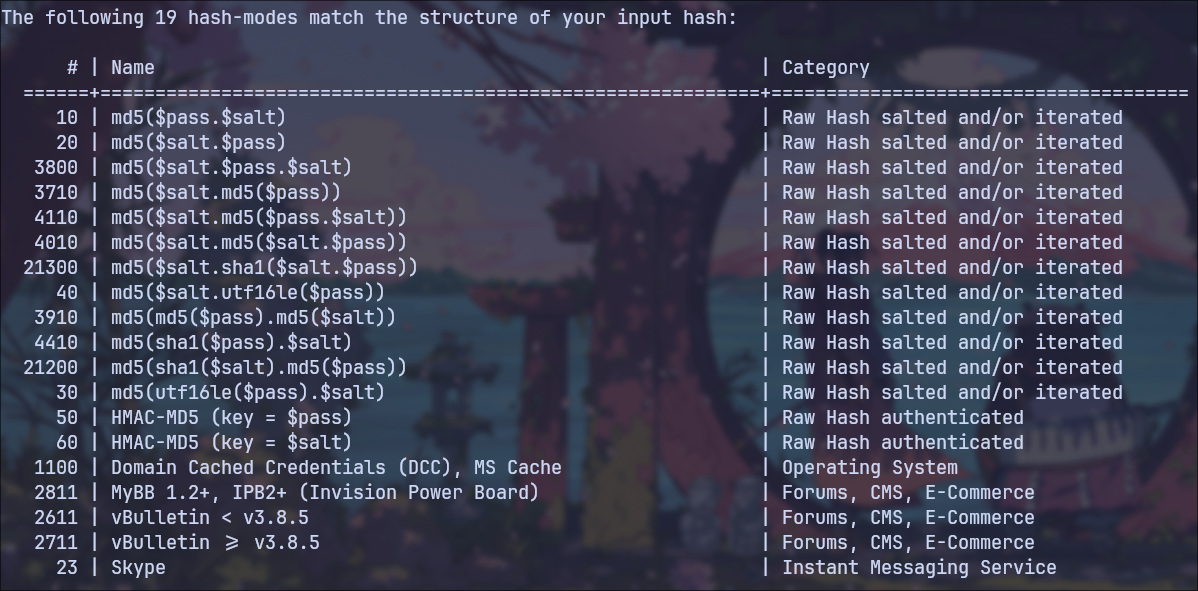
Hashcat
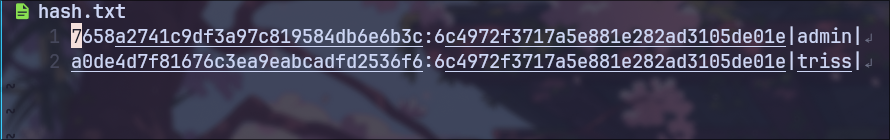
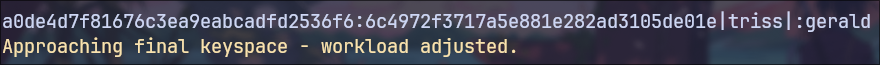
Using Hashcat, I managed to crack the password hash for the user triss.
FTP
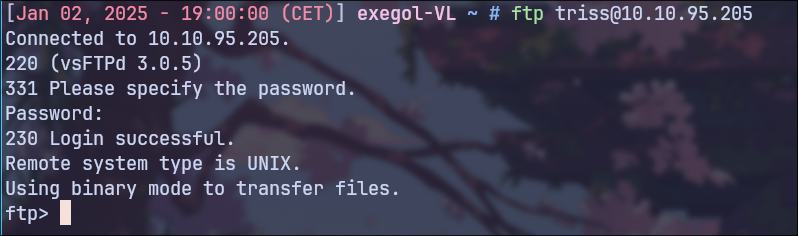
FTP Access
SSH login is not possible with the cracked password, as key-based authentication is enforced. However, I was able to log in to the FTP server.
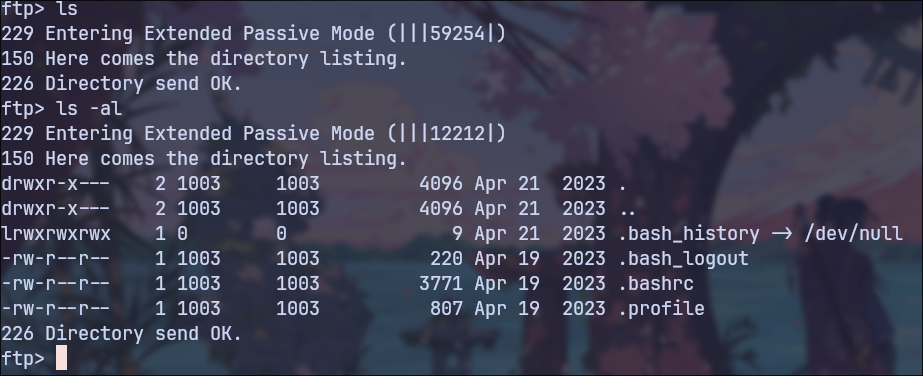
SSH Key Upload
The FTP server’s root directory is the home directory of the user triss, which allows me to upload my public SSH key.
| |
Now I can log in via SSH using my private key:
| |
Privilege Escalation
User Flag
There is no user flag in triss’s home directory. However, due to a reference to “The Witcher” by Andrzej Sapkowski in the challenge, I guessed that the password for the user jennifer is the same as for triss. This allowed me to obtain the user flag.
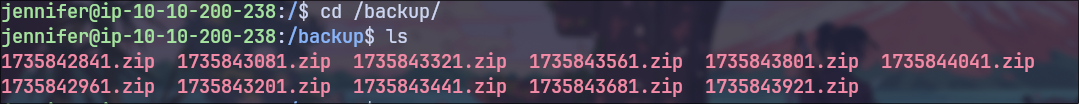
/backup Directory
After running LinPEAS, I discovered the /backup directory.
John the Ripper
I found backup copies of /etc/passwd and /etc/shadow. I used John the Ripper to crack the password for the user sa:
| |
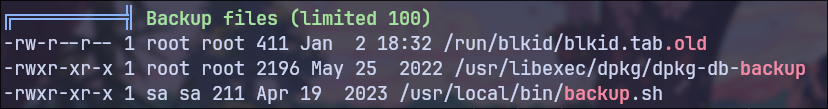
backup.sh
I discovered a backup script owned by the user sa
| |
After modifying the script and executing it, I was able to escalate privileges and gain root access.
| |
“Wiem, za rzadko się modlę, może kiedyś dorosnę
Gorzkie słowa jak ogień rzucają na twarzy cień
Proszę, daj mi melodię, niech zapełni sto wspomnień
Moje wersy jak fobie będą zawsze obok mnie…” ~Inee
